78% of Surveyed Organizations Targeted by Ransomware
Our annual global study of IT and security professionals reveals escalating threats, longer recovery times, and widespread business disruption, despite a modest reduction in successful attacks.
Ransomware-related challenges persist as agentic AI attacks gain traction
The spread of generative AI, an increasing concern about agentic AI attacks, rising geopolitical tensions, global regulatory shifts … many new developments are complicating the cyber threat landscape. How well are organizations adapting? The
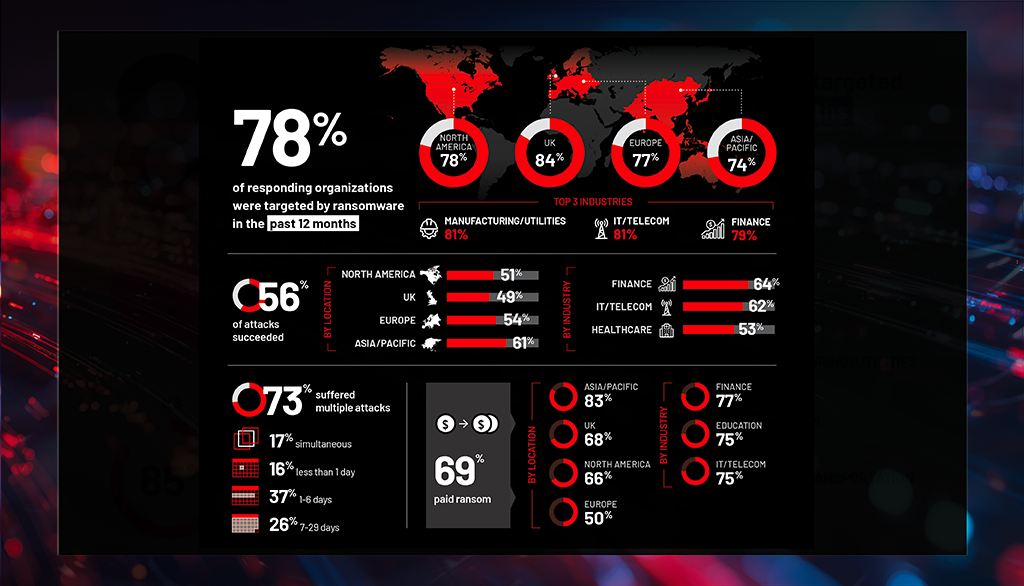
Study reveals new attack insights from organizations around the world
There’s good news in this year’s findings: Ransomware attack frequency and success saw modest decreases. But as former US National Cyber Director and Semperis Strategic Advisor Chris Inglis told us, “Now is not the time for complacency. True regret isn’t not knowing what you should have done; it’s not having done what you knew was needed and had the means to do.”
Read moreof companies that were successfully attacked by ransomware were attacked multiple times—32% three or more times.
of ransomware victims that paid ransom did so multiple times; 29% paid three times or more.
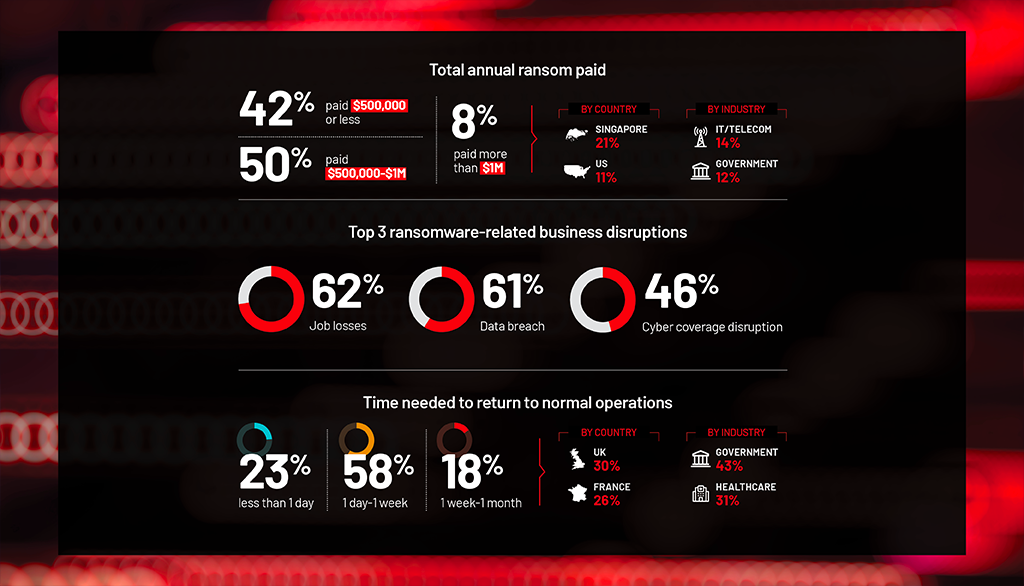
Disruptions and lagging recovery times threaten business resilience
Despite gains in fending off attacks, business disruptions are continuous, persistent, and potentially life-threatening. And organizations are taking longer to return to business as normal.
“If you don’t properly secure your environment, you’re going to pay more for your insurance—or you’re going to become uninsurable,” warns Jeff Wichman, Semperis Director of Incident Response. To protect your investment, he says, “You need to determine what your weak spots are, think of different tactics that an attacker might throw at you, start building from there—and then test, test, test.”
of victims did not receive usable decryption keys
of ransomware victims needed more than 1 day to return to normal operations
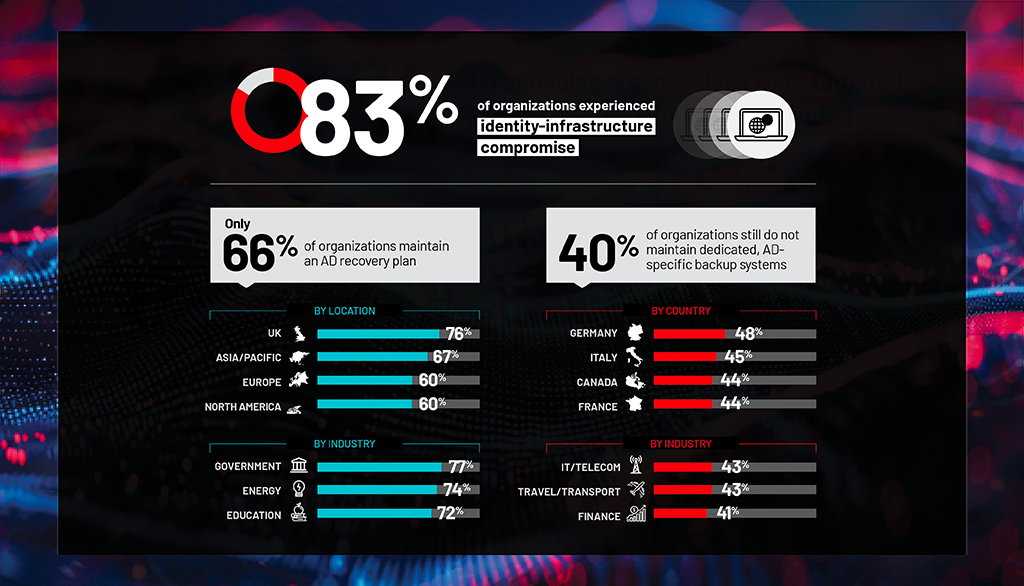
IAM infrastructure remains a top target
With threat actors targeting the identity and access management (IAM) infrastructure itself, and credential abuse ranking as a top attack vector, organizations must strengthen their IAM defenses to stay ahead of attackers.
Yet despite 90% of respondents telling us that they have implemented an Identity Threat Detection and Response (ITDR) strategy, a much smaller percentage include AD recovery procedures in their disaster recovery plan or maintain dedicated, AD-specific backup systems—both key parts of effective ITDR. That’s a gap that attackers will be more than happy to exploit.
Organizations note challenges to cybersecurity, business resilience
Organizations across the globe still see cyberattacks as the biggest threat to business resilience, and an increase in the frequency and sophistication of those attacks is their top cybersecurity concern.
Download reportExperts offer insights into ransomware resilience
What can organizations do to prepare for the new generation of AI-driven attacks? Our panel of experts weighs in on steps you can take today to reduce ransomware threats that exploit legacy vulnerabilities and the identity infrastructure—organizations’ other two top cybersecurity concerns—while managing business resilience challenges, including regulatory compliance.
Learn moreMore resources
Learn more about how to prevent, detect, and respond to identity-based attacks.











